It will allow us to intercept different requests, modify them and then forward them to the Web Page.
Configuring Burp Suite as a Proxy on Firefox
Step 1
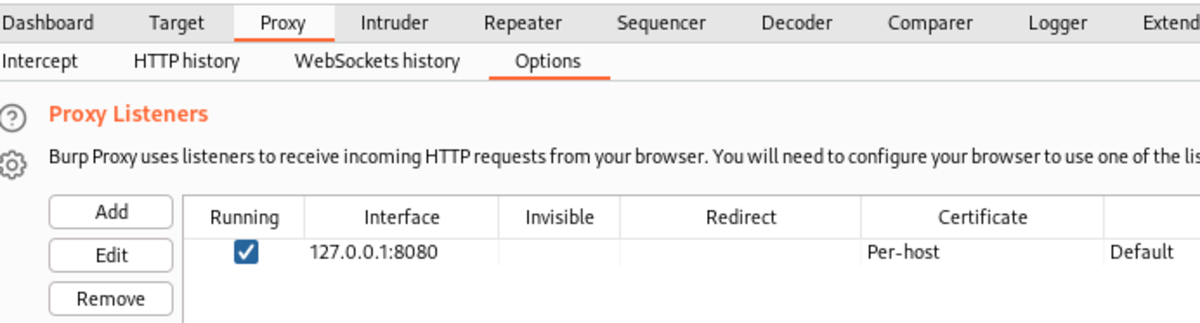
Open up the Burp Suite GUI tool and navigate to options under the Proxy tab Under “Proxy Listeners”, add the interface as 127.0.0.1:8080 (if not already set)
Step 2
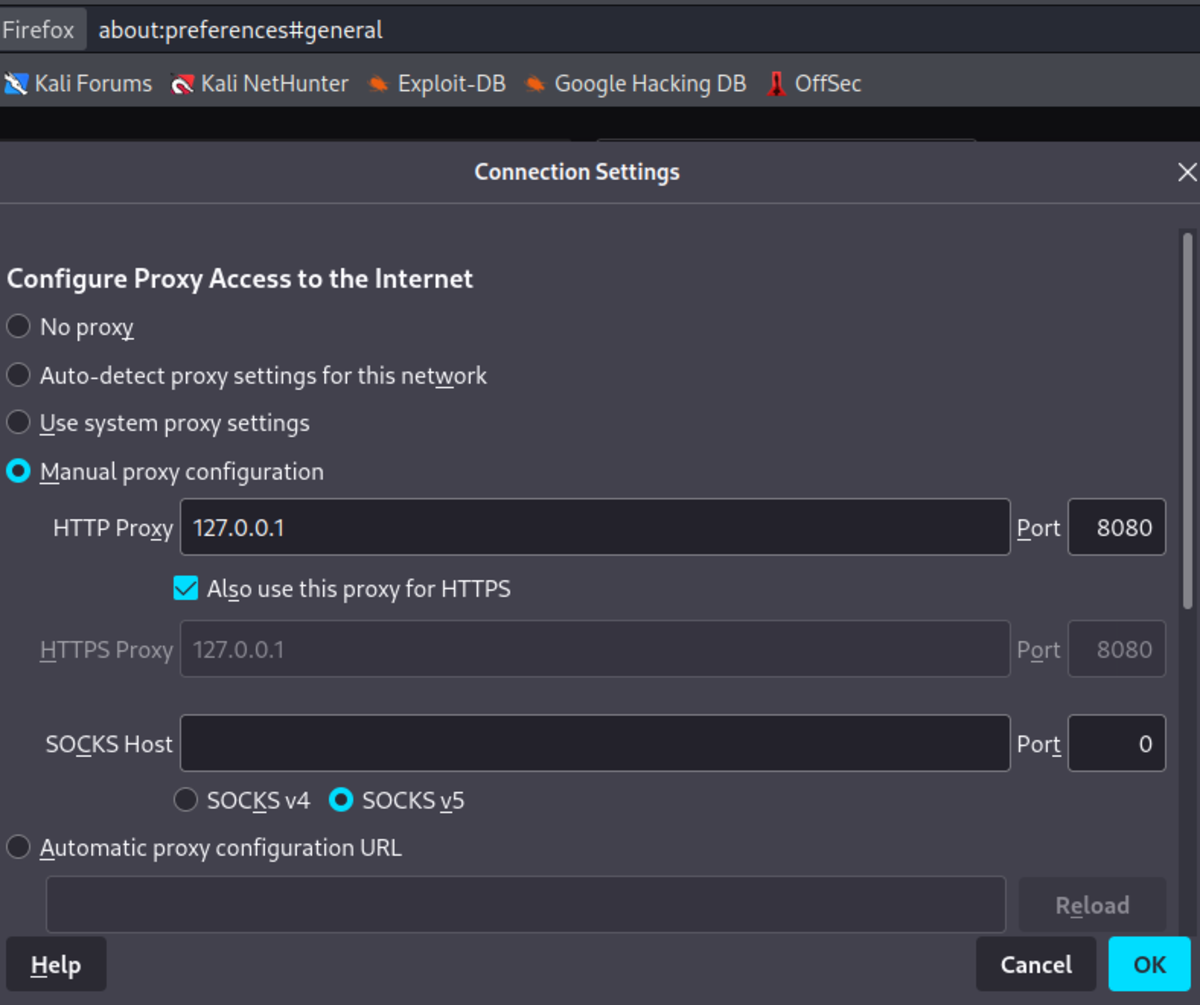
Start your web browser and navigate to Settings →General →Network Settings Under Configure proxy access settings use manual proxy configuration and add the same interface that we used above. NOTE:
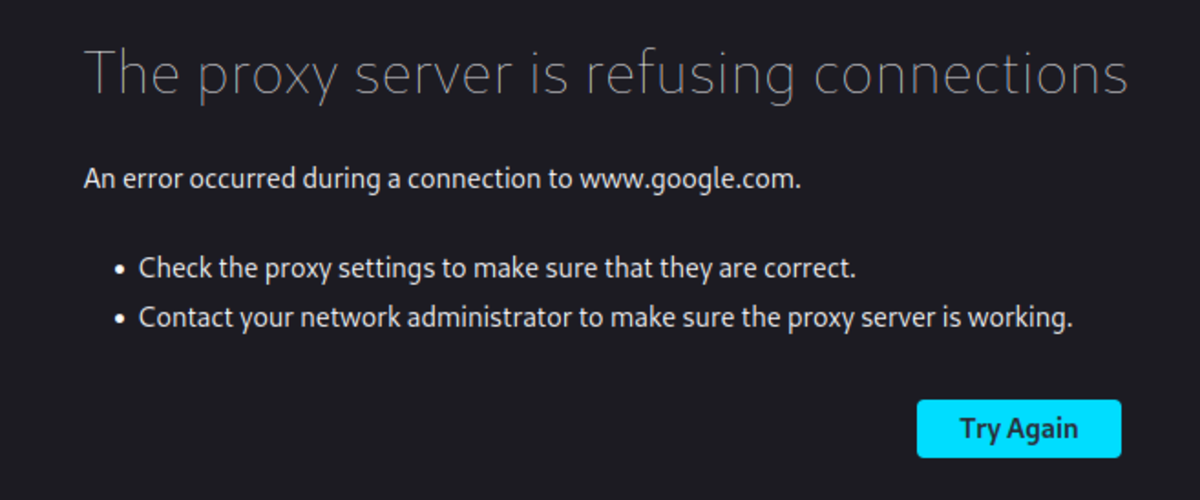
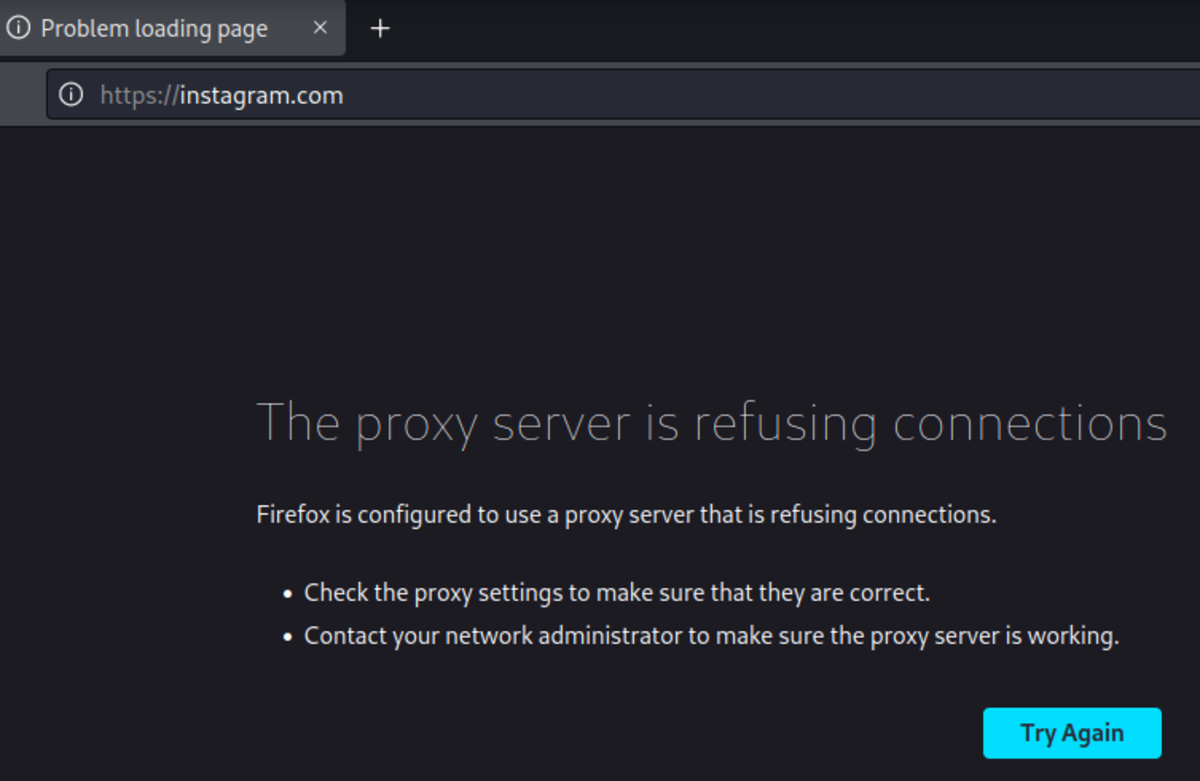
Now at this stage, you can access any “HTTP” website but when you open an “HTTPS” website you will get this type of error.
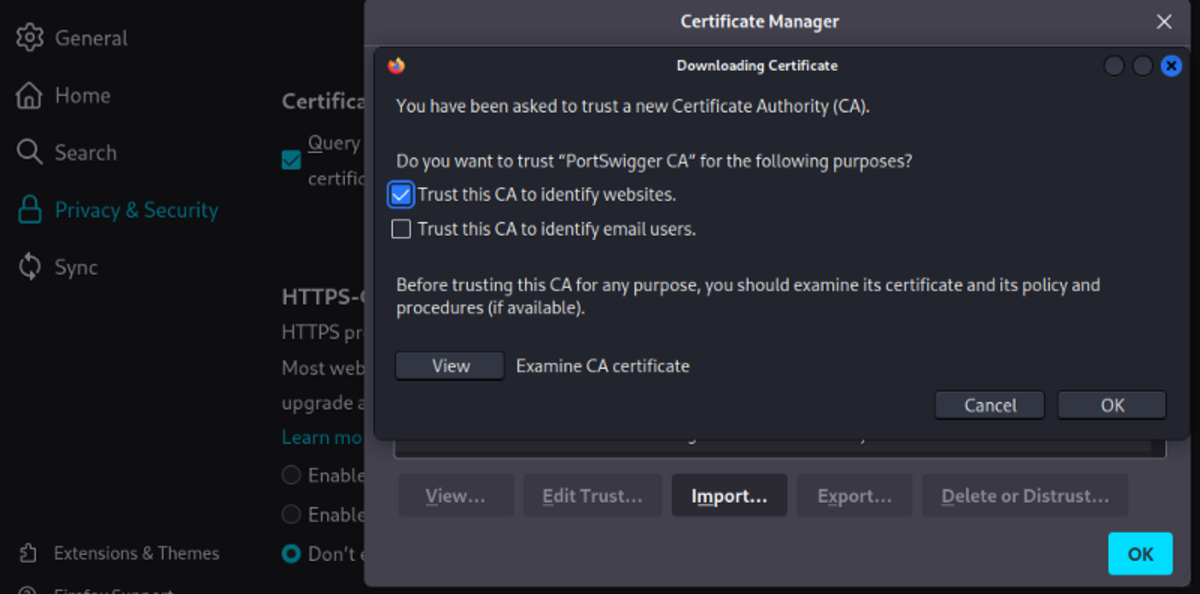
To resolve this issue you must download the Burp CA certificate and add it to our Firefox certificates.
Steps to Resolve the Above Issue
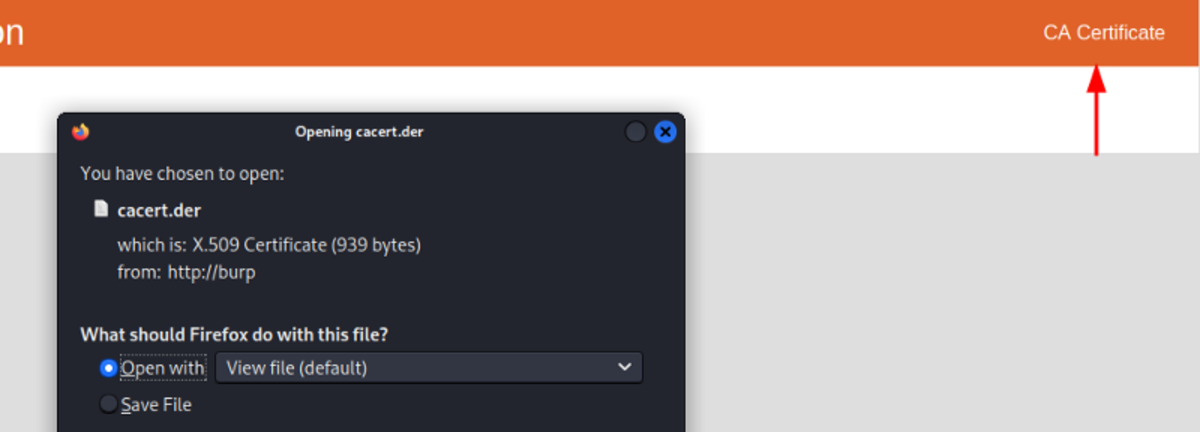
Navigate to “http://burp” & download the “cancer.der” certificate. Import the certificate to Firefox by navigating to Settings →Privacy & Security →Certificates (View Certificates) →Authorities (Import) Now you can access any website no matter whether it uses “HTTP” or “HTTPS” protocol.
Commonly Used Options in Burp Suite
Note: I will be using owaspbwa vulnerable web pages to showcase the examples.
Intercept
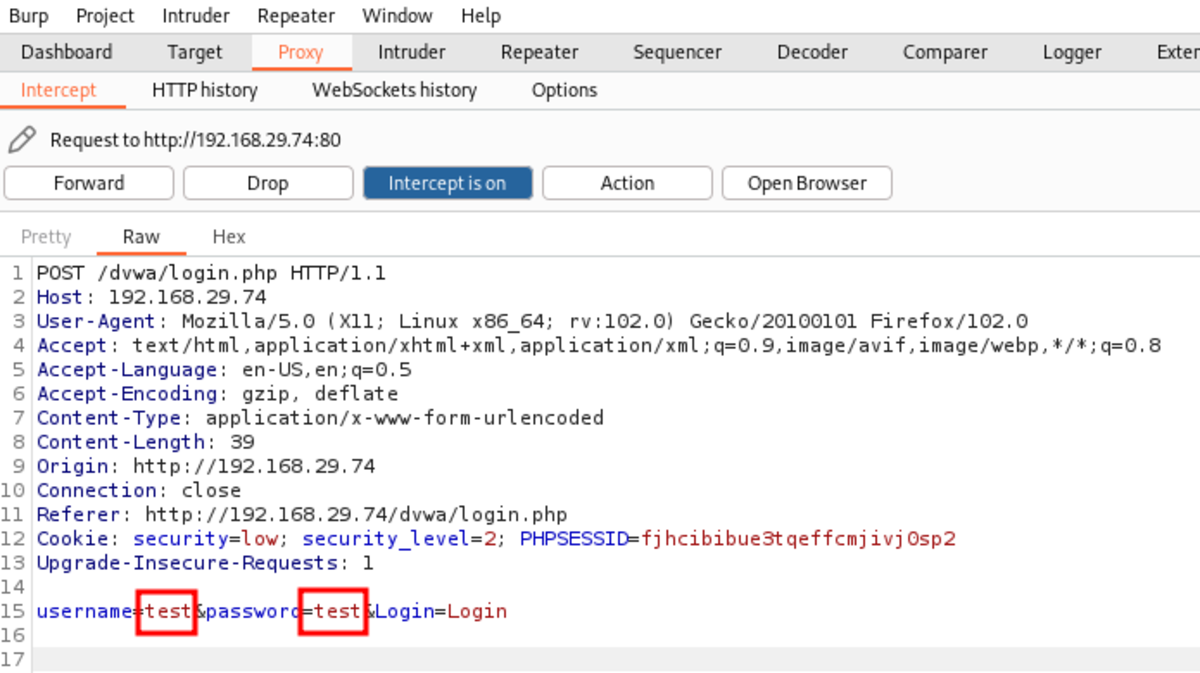
Let’s consider the dvwa page in the owaspbwa vulnerable machine as our example.
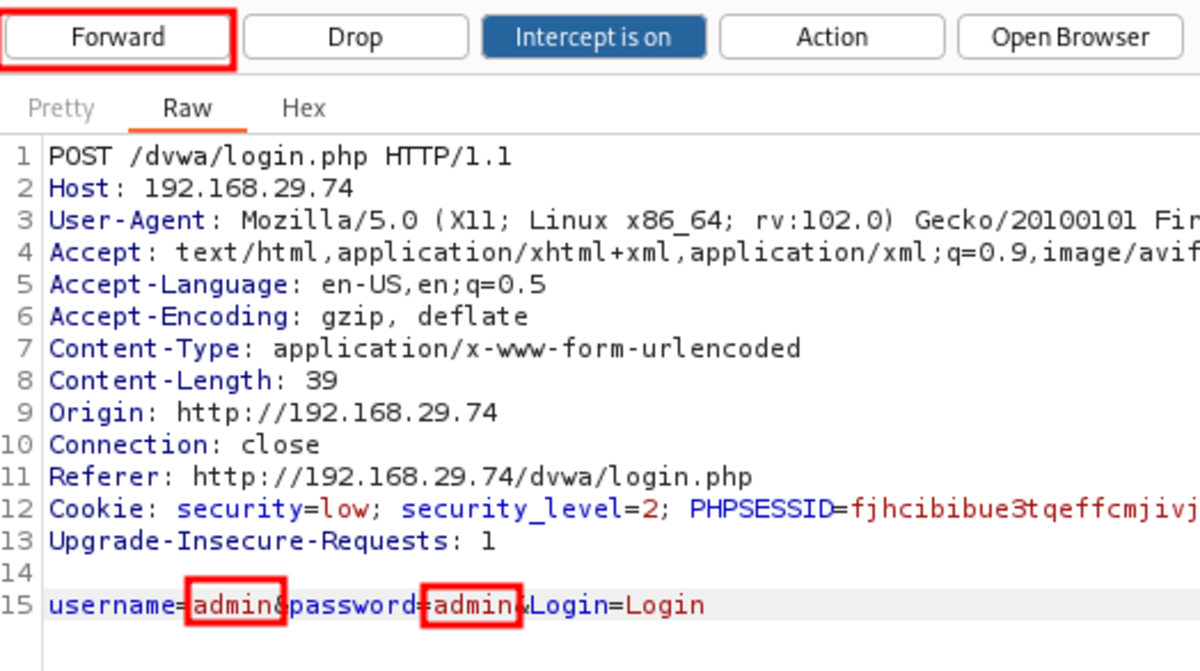
If the intercept is turned on, then Burp Suite will block the traffic going out and will display the request under the Proxy→Intercept tab in the Burp Suite application. Now you can modify the HTTP headers & other values then forward the request to see the changes made to the website.
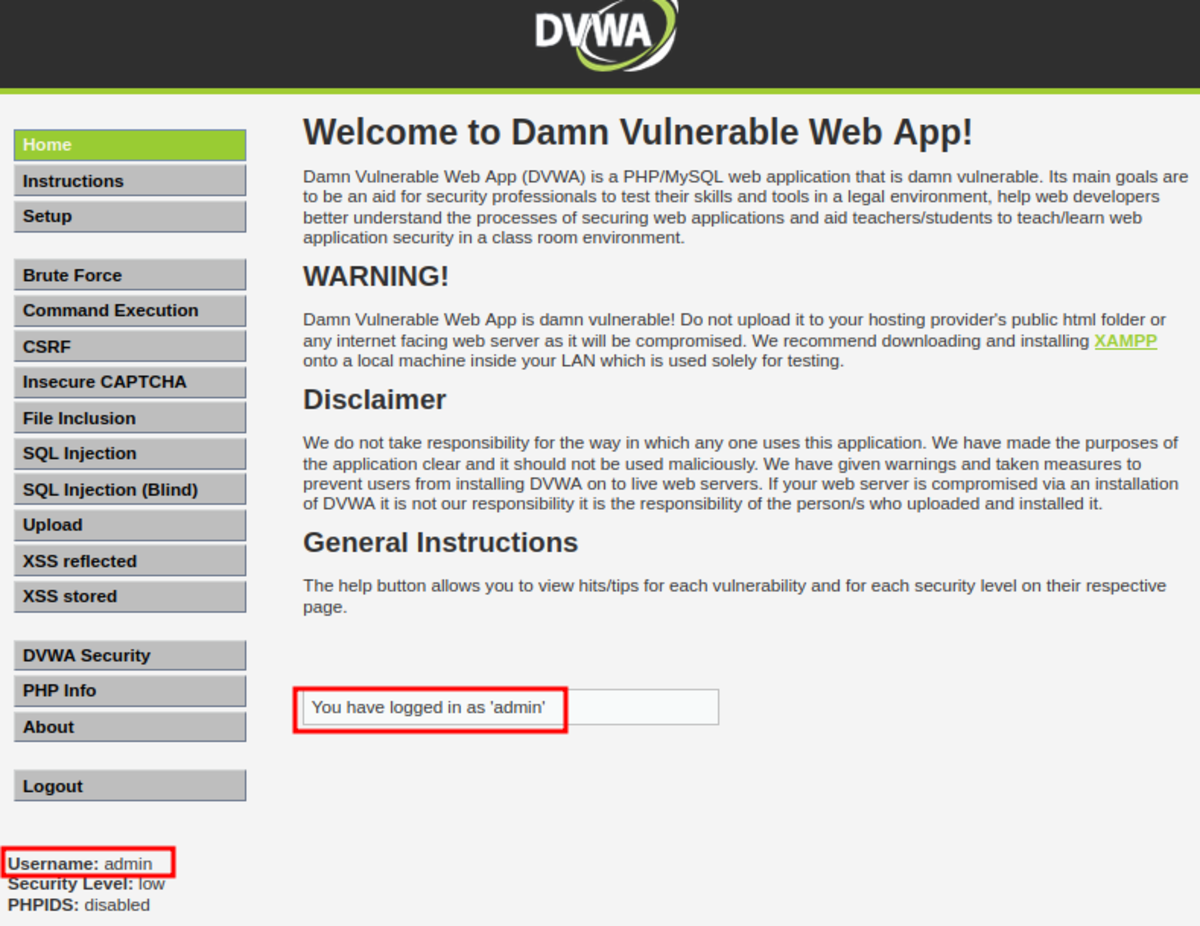
Here we are going to change the username & password fields to “admin” then forward the request & turn off the intercept.
Repeater
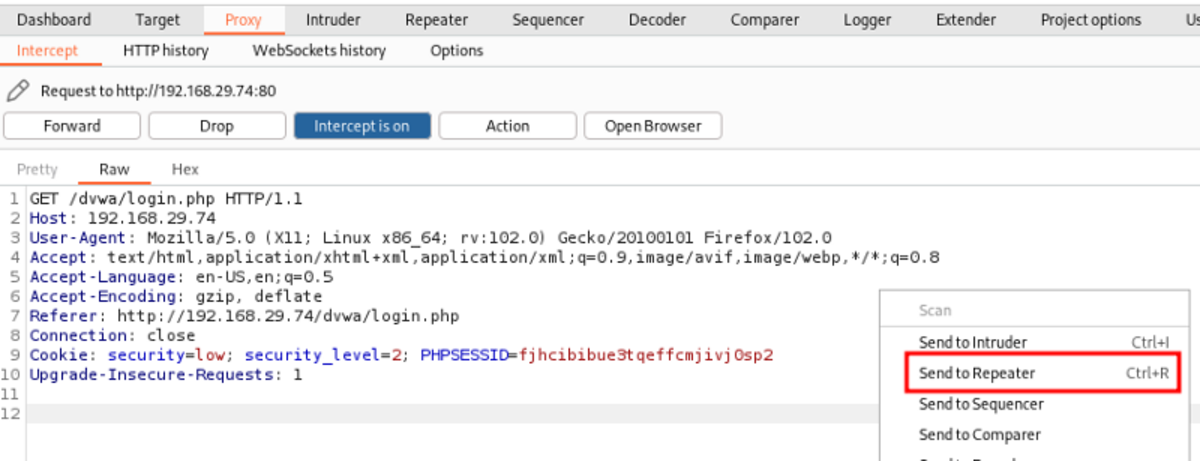
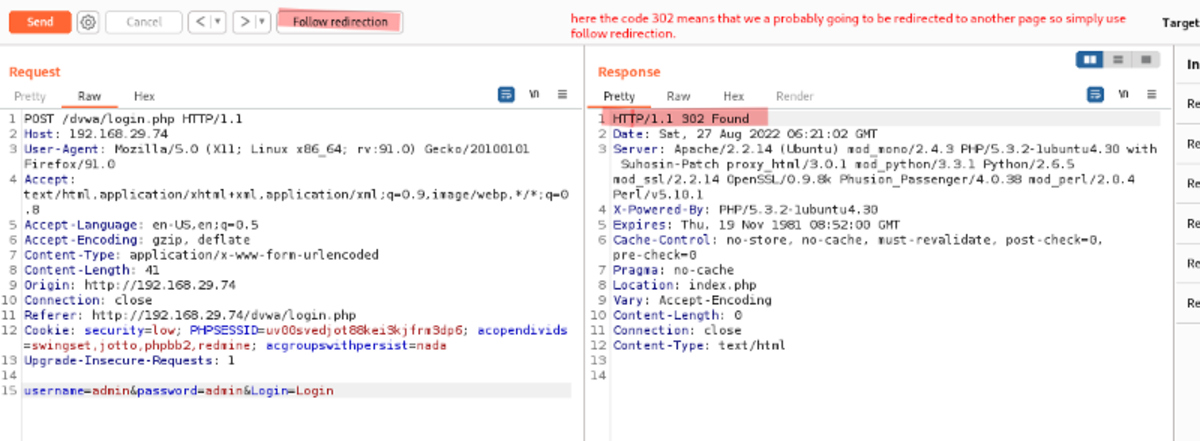
With the help of a repeater, you can send a request as many times as you want with or without modification. As an example, let’s reload the dvwa login page and intercept it in our Burp Suite again. Now right-click and send the intercepted request to the repeater.
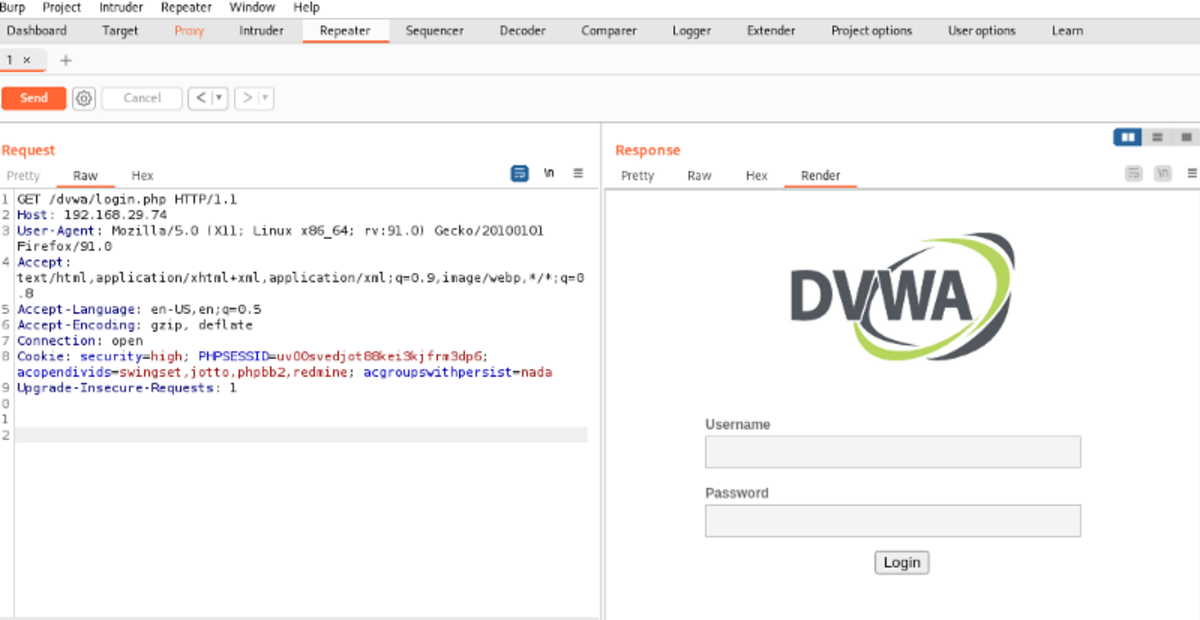
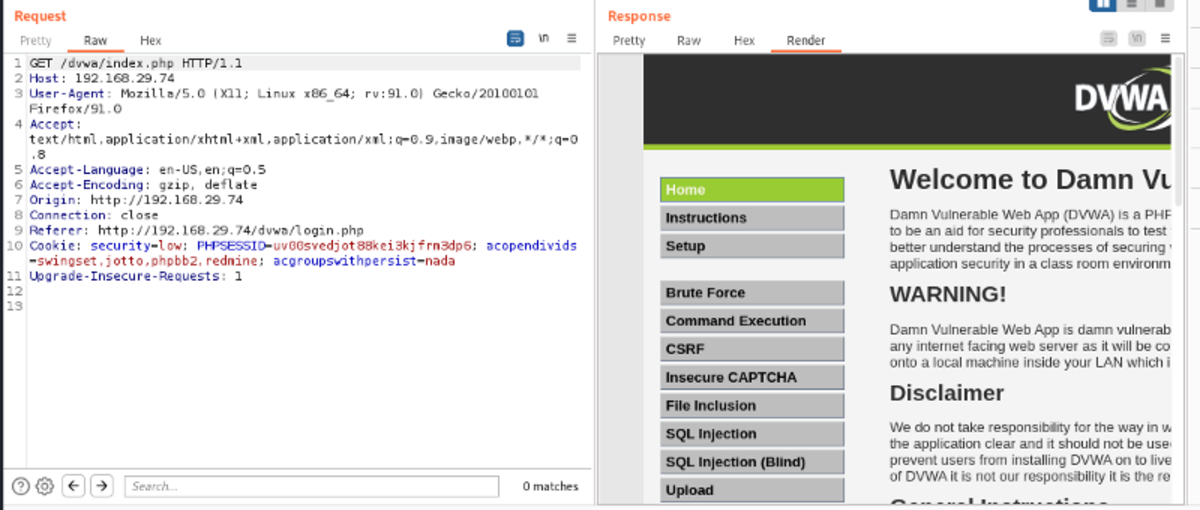
You can edit the request here, and when you submit it, you can see the changes that immediately appear on the website (under render) or the response code (under Pretty). Let’s reload the login page → send to repeater → modify username & password to ‘admin’ →follow the redirection.
Intruder
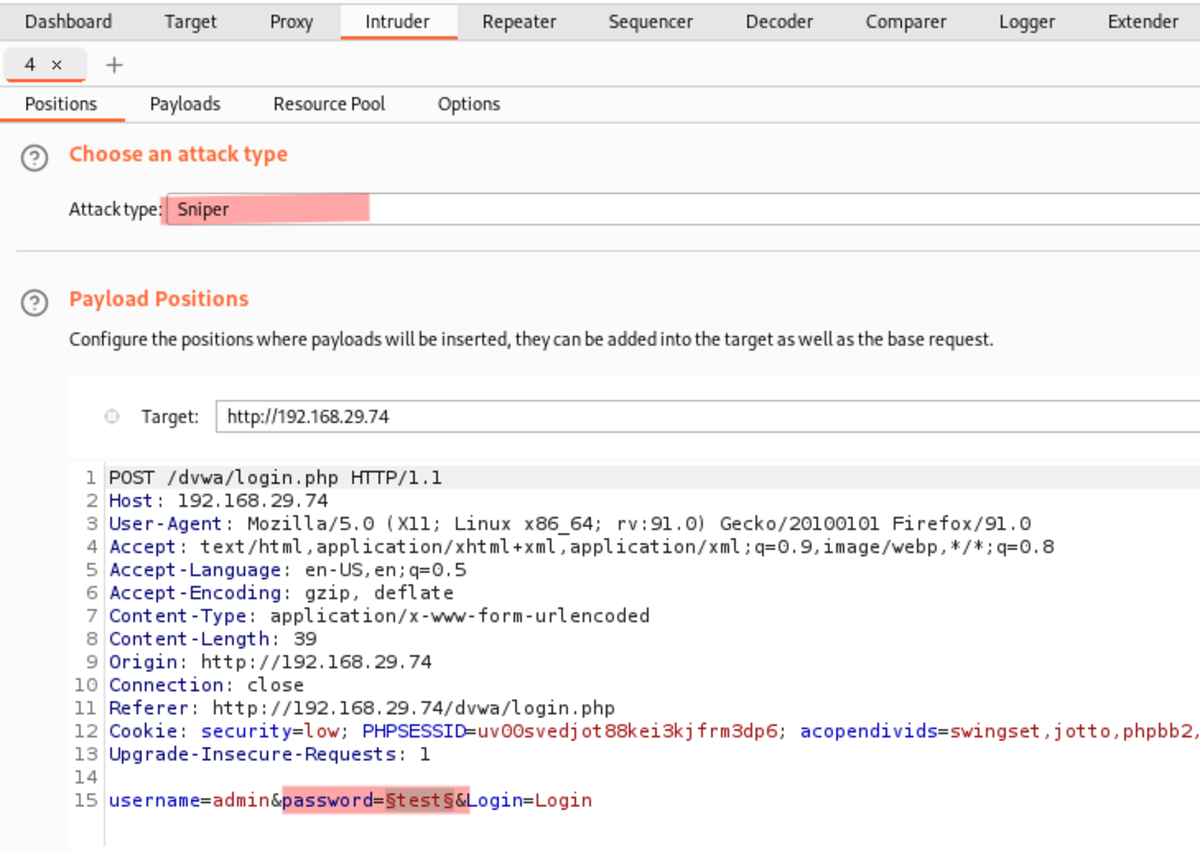
It can be considered as something made for brute-force attacks. Users can edit any section of the request and forward it, but we can also update specific portions of the request by reading from our list.
Example
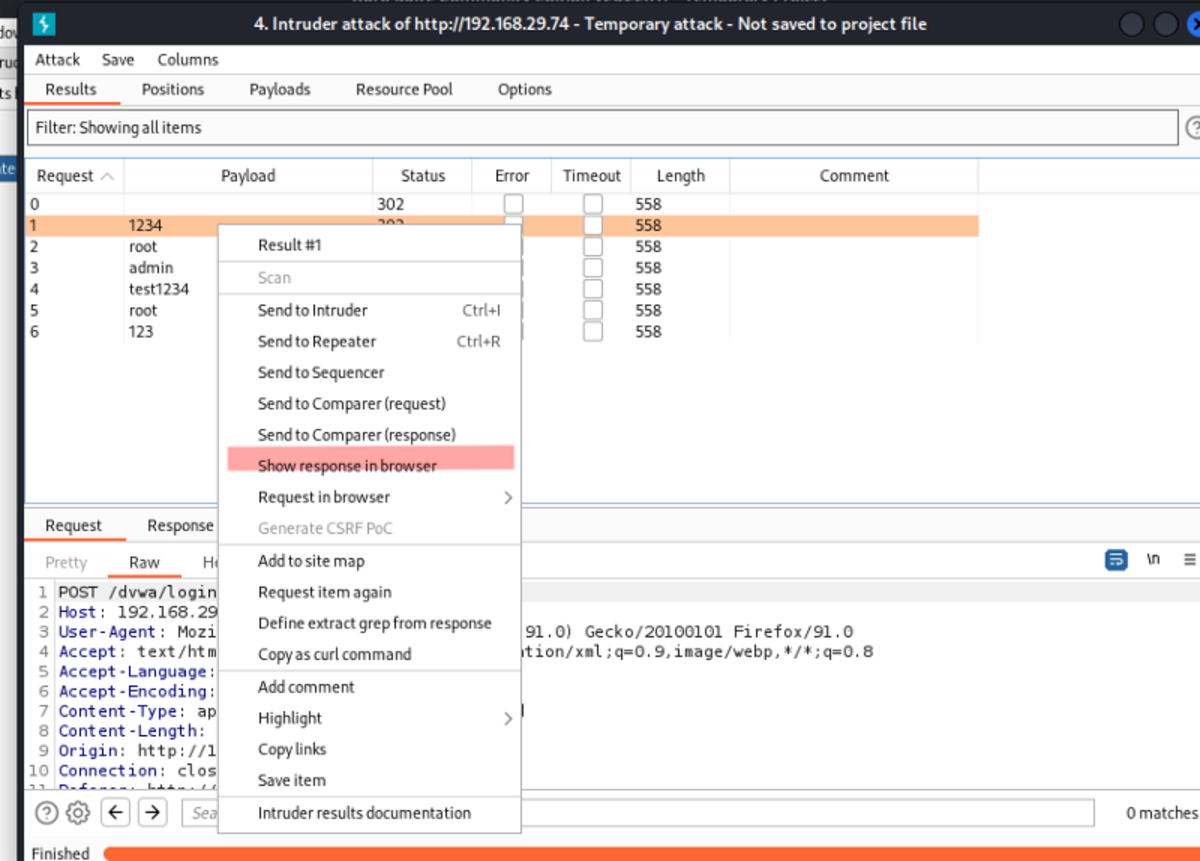
For the same login page (/dvwa/login.php) Reload the login page → send to Intruder →Add payloads→specify target & attack to perform → start the attack.
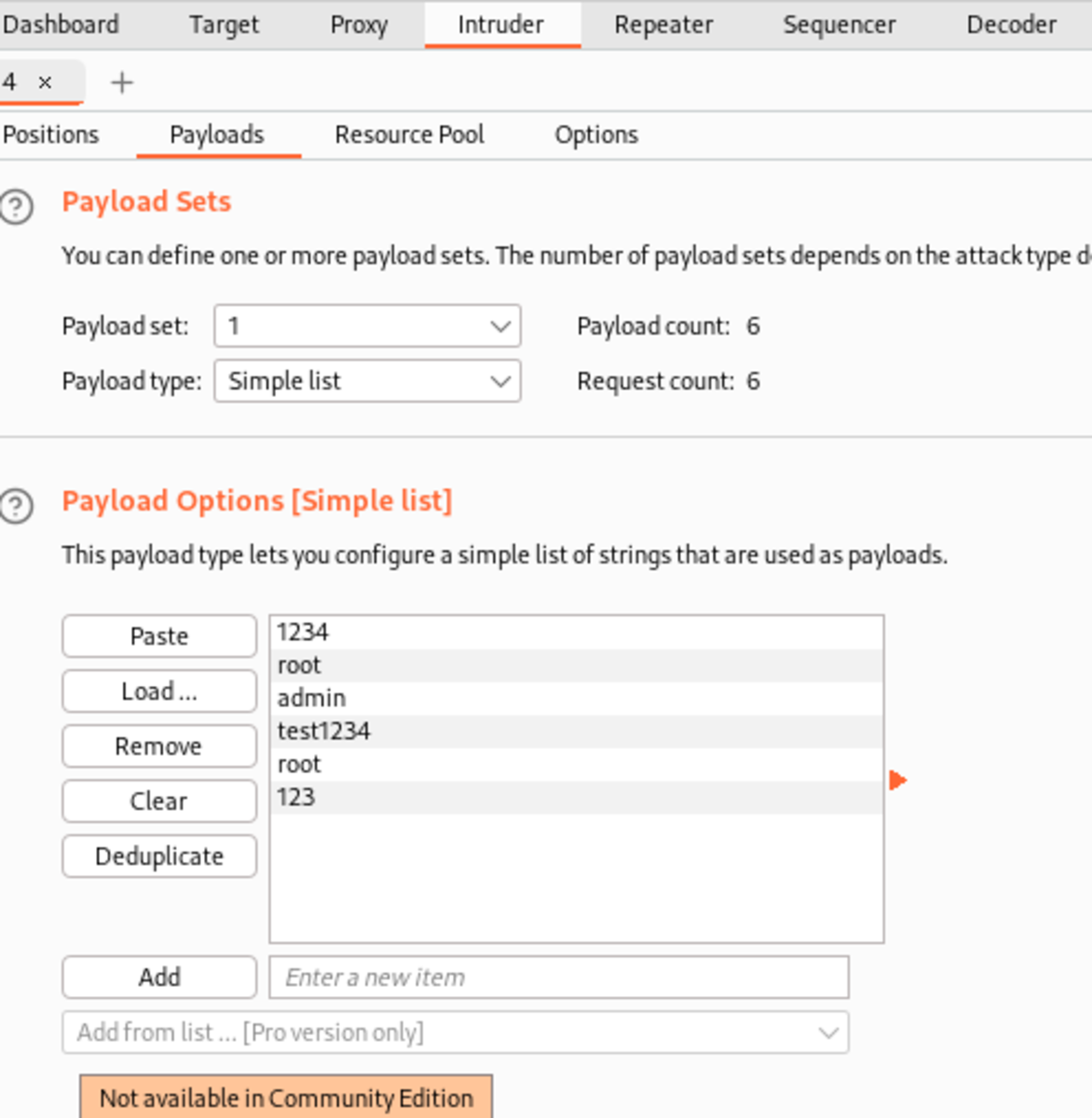
Add Your Payloads
Specify the target field and the type of attack you want to perform.
It’s now time to start the attack.
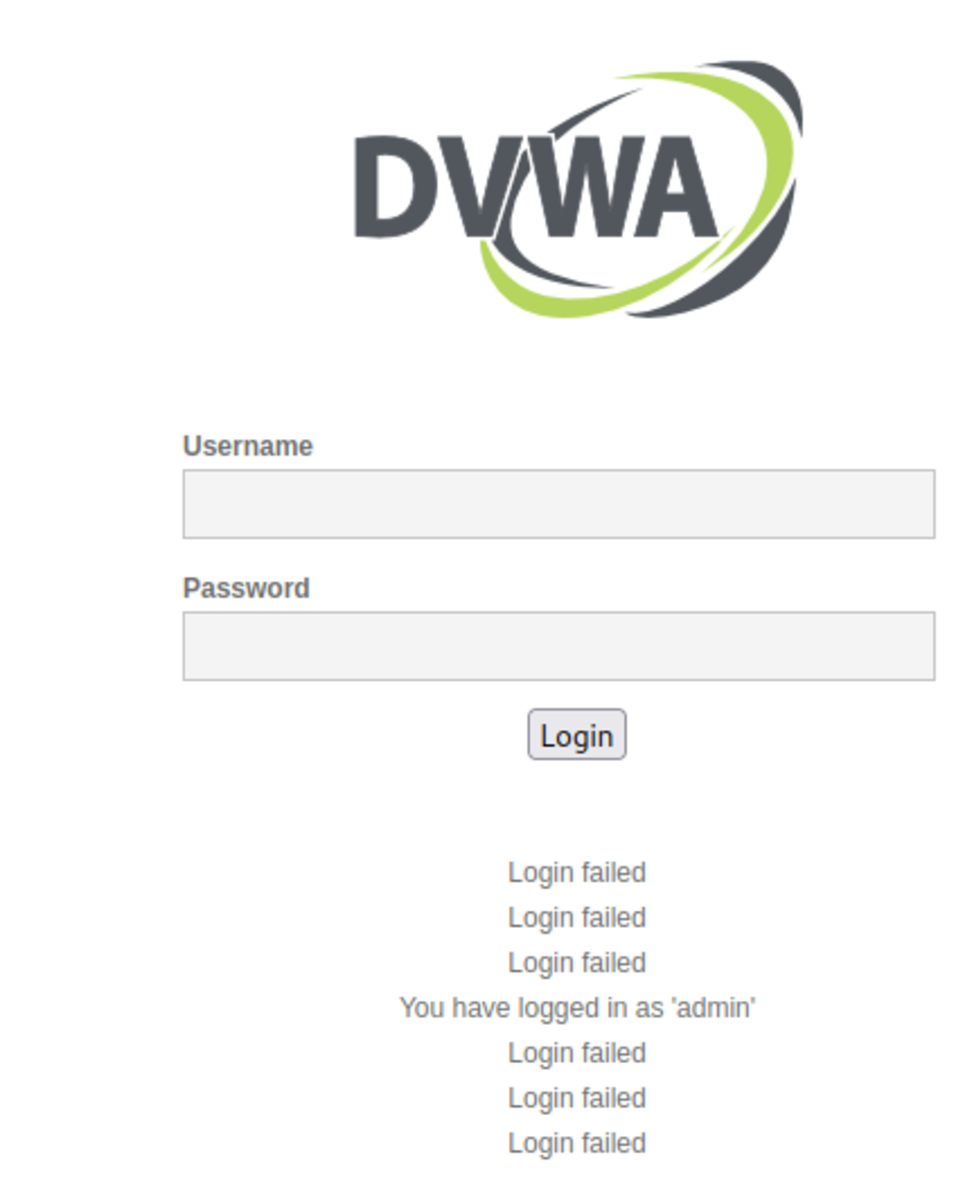
Copy and paste the URL into the browser (make sure to turn off the intercept)
We can see that the 4th word matched our password which was “admin” (the 0th one was an empty string).
- 30+ Standard Linux Commands for Beginner or Intermediate Users
- Bug Bounty Hunting With Burp Suite (Intercept, Repeater & Intruder)
- Broken Access Control (Tryhackme and Owaspbwa)
- Html Injection (Tryhackme & Owaspbwa)
- Command Injection (Tryhackme & Owaspbwa)
- Website Enumeration and Information Gathering [Part 1]
- Website Enumeration & Information Gathering [Part 2]
- Brute Force Attack (Owaspbwa Lab, Hydra Tool)
- Sensitive Data Exposure (Tryhackme)
- Broken Authentication (Tryhackme and Owaspbwa)
- Security Misconfiguration (Tryhackme) This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel